- Intune Cisco Anyconnect Vpn Profile
- Cisco Anyconnect Intune Windows 10
- Intune Cisco Anyconnect Download
- Intune Cisco Vpn
- Cisco Anyconnect Windows 10 Download
- Intune Per App Vpn Cisco Anyconnect
I’m really curious if it’s just me, or does Intune seem to have a very slow feedback loop as well as slow deployments. I deploy a policy/configuration, and it apparently gets pushed immediately using WNS, but then your stuck waiting for the dashboard to update for what can be 15 or 20 minutes. WebSecurity anyconnect-win-version-websecurity-webdeploy-k9.exe anyconnect-win-version-websecurity-predeploy-k9.msi ISEPosture anyconnect-win- version -iseposture-webdeploy-k9.msi anyconnect-win- version -iseposture-predeploy-k9.msi. Yes, i have deployed Cisco Systems VPN via intune. As u/Fwcasey has said you need to first install the Dell sonic wall VPN client, and then Cisco VPN. I created a third installation package that did the registry edits and placed the PCF file in the correct directory.
By downloading an XML file from Umbrella and then uploading it to your Intune system, Intune is able to push configuration information to both the Cisco Security Connector (CSC) and Umbrella so that your iOS device is registered with Umbrella. The result is that your iOS device is protected by Umbre.
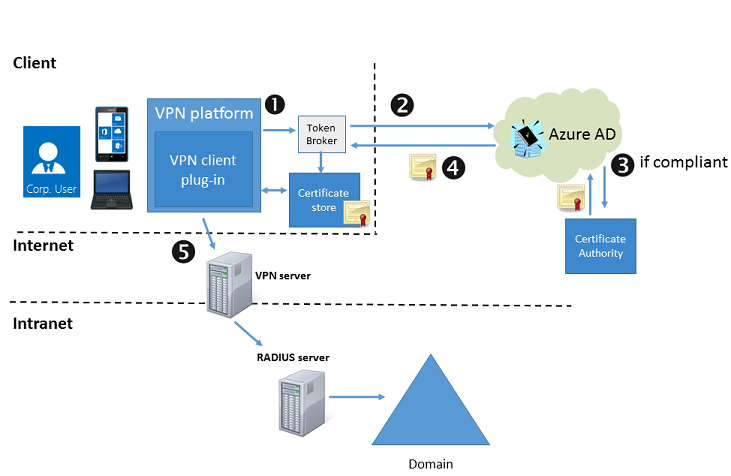
-->Intune integrates with network access control (NAC) partners to help organizations secure corporate data when devices try to access on-premises resources.
Important
NAC is not currently supported for Android Enterprise Fully Managed or Android Enterprise Dedicated devices.
How do Intune and NAC solutions help protect your organization resources?
NAC solutions check the device enrollment and compliance state with Intune to make access control decisions. If the device isn't enrolled, or is enrolled and not compliant with Intune device compliance policies, then the device should be redirected to Intune for enrollment, or for a device compliance check.
Example
If the device is enrolled and compliant with Intune, the NAC solution should allow the device access to corporate resources. For example, users can be allowed or denied access when trying to access corporate Wi-Fi or VPN resources.
Intune Cisco Anyconnect Vpn Profile
Feature behaviors
Cisco Anyconnect Intune Windows 10
Devices that are actively syncing to Intune can't move from Compliant / Noncompliant to Not Synched (or Unknown). The Unknown state is reserved for newly enrolled devices that haven't been evaluated for compliance yet.
For devices that are blocked from access to resources, the blocking service should redirect all users to the management portal to determine why the device is blocked. If the users visit this page, their devices are synchronously reevaluated for compliance.
NAC and Conditional Access
NAC works with Conditional Access to provide access control decisions. For more information, see Common ways to use Conditional Access with Intune.
How the NAC integration works
The following list is an overview on how NAC integration works when integrated with Intune. The first three steps, 1-3, explain the onboarding process. Once the NAC solution is integrated with Intune, steps 4-9 describe the ongoing operation.
- Register the NAC partner solution with Azure Active Directory (AAD), and grant delegated permissions to the Intune NAC API.
- Configure the NAC partner solution with the appropriate settings including the Intune discovery URL.
- Configure the NAC partner solution for certificate authentication.
- User connects to corporate Wi-Fi access point or makes a VPN connection request.
- NAC partner solution forwards the device information to Intune, and asks Intune about the device enrollment and compliance state.
- If the device isn't compliant or isn't enrolled, the NAC partner solution instructs the user to enroll or fix the device compliance.
- The device tries to reverify its compliance and enrollment state when applicable.
- Once the device is enrolled and compliant, NAC partner solution gets the state from Intune.
- Connection is successfully established which allows the device access to corporate resources.
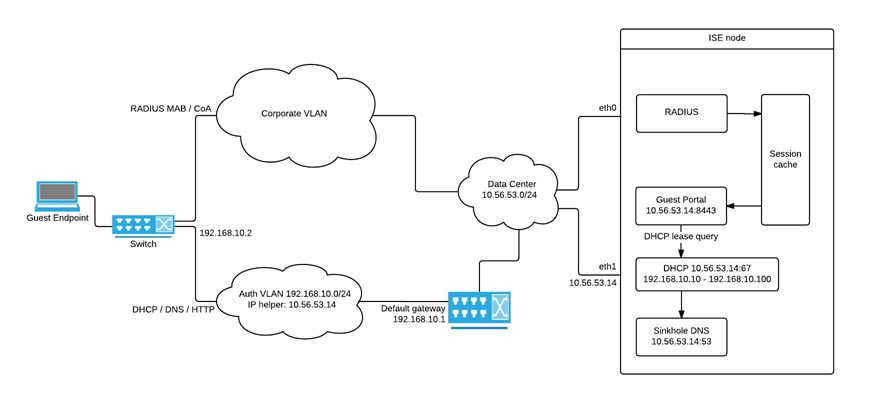
Use NAC for VPN on your iOS/iPadOS devices
NAC is available on the following VPNs without enabling NAC in the VPN profile:
- NAC for Cisco Legacy AnyConnect
- F5 Access Legacy
- Citrix VPN
NAC is also supported for Cisco AnyConnect, Citrix SSO, and F5 Access.
To enable NAC for Cisco AnyConnect for iOS
- Integrate ISE with Intune for NAC as described in the link below.
- Set the Enable Network Access Control (NAC) setting in the VPN profile to Yes.
To enable NAC for Citrix SSO
Intune Cisco Anyconnect Download

- Use Citrix Gateway 12.0.59 or higher.
- Users must have Citrix SSO 1.1.6 or later installed.
- Integrate NetScaler with Intune for NAC as described in the Citrix product documentation.
- In the VPN profile, select Base settings > Enable Network Access Control (NAC) > select I agree.
To enable NAC for F5 Access
- Use F5 BIG-IP 13.1.1.5 or later.
- Integrate BIG-IP with Intune for NAC. The Overview: Configuring APM for device posture checks with endpoint management systems F5 guide lists the steps.
- In the VPN profile, select Base settings > Enable Network Access Control (NAC) > select I agree.
The VPN connection is disconnected every 24 hours for security reasons. The VPN can immediately be reconnected.
We're working with our partners to release a NAC solution for these newer clients. When solutions are ready, this article will be updated with additional information.
Next steps
AnyConnect implements the Samsung Knox VPN framework and is compatible with the Knox VPN SDK. It's recommended to use Knox version 2.2 and above with AnyConnect. All operations from IKnoxVpnService are supported. For detailed description of each operation, please see the IKnoxVpnService documentation published by Samsung.
Knox VPN JSON Profile
As required by the Knox VPN framework, each VPN configuration is created using a JSON object. This object has provides three main sections of the configuration:
- General attributes - 'profile_attribute'
- Vendor (AnyConnect) specific attributes - 'vendor'
- Knox specific profile attributes - 'knox'
Supported profile_attribut Fields
- profileName - Unique name for the connection entry to appear in the connection list of the AnyConnect home screen and the Description field of the AnyConnect connection entry. We recommend using a maximum of 24 characters to ensure that they fit in the connection list. Use letters, numbers, or symbols on the keyboard displayed on the device when you enter text into a field. The letters are case-sensitive.
- vpn_type - The VPN protocol used for this connection. Valid values are:
- ssl
- ipsec
- vpn_route_type - Valid values are:
- 0 – System VPN
- 1 – Per-app VPN
For more information regarding the common profile attributes, please see the Samsung KNOX Framework Vendor Integration Guide.
AnyConnect specific configuration is specified via 'AnyConnectVPNConnection' key inside inside the 'vendor' section. Sample:
Supported AnyConnectVPNConnection Fields
Intune Cisco Vpn
- host - The domain name, IP address, or Group URL of the ASA with which to connect. AnyConnect inserts the value of this parameter into the Server Address field of the AnyConnect connection entry.
- authentication - (optional) Only applies when vpn_type (in profile_attributes) is set to 'ipsec'. Specifies the authentication method used for an IPsec VPN connection Valid values are:
- EAP-AnyConnect (default value)
- EAP-GTC
- EAP-MD5
- EAP-MSCHAPv2
- IKE-PSK
- IKE-RSA
- IKE-ECDSA
- ike-identity - Used only if authentication is set to EAP-GTC, EAP-MD5, or EAP-MSCAPv2. Provides the IKE identity for these authentication methods.
- usergroup (optional) The connection profile (tunnel group) to use when connecting to the specified host. If present, used in conjunction with HostAddress to form a Group-based URL. If you specify the Primary Protocol as IPsec, the User Group must be the exact name of the connection profile (tunnel group). For SSL, the user group is the group-url or group-alias of the connection profile.
- certalias (optional)- KeyChain alias of a client certificate that should be imported from Android KeyChain. The user must acknowledge an Android system prompt before the cert could be used by AnyConnect.
- ccmcertalias (optional)- TIMA alias of a client certificate that should be imported from the TIMA certificate store. No user action is necessary for AnyConnect to receive the cert. Please note: this certificate must have been explicitly whitelisted for use by AnyConnect (e.g. using the Knox CertificatePolicy API).
Inline VPN Packet App Metadata
Cisco Anyconnect Windows 10 Download
Inline app metadata for VPN packets is an exclusive feature available on Samsung Knox devices. It is enabled by MDM and provides AnyConnect with source application context for enforcing routing and filtering policies. It is required for implementing certain per-app VPN filtering policies from the VPN gateway on Android devices. Policies are defined to target specific application id or groups of apps via wildcarding and is matched against the source application id of each outbound packet.
MDM dashboard should provide administrators with an option to enable inline packet metadata. Alternatively, MDM could hardcode this option to always be enabled for AnyConnect, which will make use of it as per headend policy.
For more information on AnyConnect’s per-app VPN policies, please see the section on 'Define a Per App VPN Policy for Android Devices' in the Cisco AnyConnect Secure Mobility Client Administrator Guide.
Intune Per App Vpn Cisco Anyconnect
MDM Configuration
To enable inline packet metadata, set 'uidpid_search_enabled' to 1 in the Knox specific attribute for a configuration. Sample:
